NEW YORK (AP) - The Latest on a widespread cyberattack that is affecting companies and government systems (all times local):
6:30 p.m.
Ports operated by the Danish shipping giant A.P. Moller-Maersk are still crippled following this week’s cyberattack.
An official with the Alabama State Port Authority, James K. Lyons, says crews at the Maersk’s APM terminal in Mobile, Alabama, have been loading and unloading containers in manual mode, without the normal computerized coordination. Lyons says the APM operation at Mobile handles 1,000 to 1,500 cargo containers each day. Other terminals aren’t affected.
APM gate operations at Port Elizabeth in New Jersey are expected to remain shuttered through at least Thursday. Port Elizabeth is APM’s largest terminal on the East Coast of North America.
In Los Angeles, there’s minimal impact - but only because no ships had been scheduled to load or unload at the ATM Terminal there on Tuesday or Wednesday. There’s no estimate on when the terminal will reopen.
In a statement, Moller-Maersk acknowledged that its APM Terminals had been “impacted in a number of ports,” but the company wouldn’t provide further detail. APM has 189 port and inland facilities in 61 countries.
___
(Previously datelined Paris; all times local)
7:25 p.m.
Logistics firm FedEx says deliveries by its TNT Express subsidiary have been slowed by the global cyberattack, another sign of how major companies are struggling to deal with the fallout from an especially virulent outbreak of data-scrambling software.
In an announcement Wednesday, the company based in Memphis, Tennessee, said it had been “significantly affected” by the malicious program, which emerged in Ukraine on Tuesday before spreading around the world.
FedEx said that the domestic, regional and intercontinental operations of TNT Express, a courier delivery unit, were “largely operational, but slowed.” The company added that the impact of the cyberattack “could be material.”
FedEx shares were up 1.2 percent at $217 in New York on Wednesday.
___
7:15 p.m.
Whoever is behind the global cyberattack centered on Ukraine, they’ve made $10,000.
More than 24 hours after a new form of malicious software caused widespread disruption in Ukraine and grabbed headlines around the world, the hackers have nearly gathered 4 bitcoin, worth just over $10,000 at current prices, according to the attackers’ publicly available bitcoin wallet.
It’s a relatively meager haul given the virulence of the malware outbreak, and some researchers are citing it as further evidence that the cyberattack was intended not to make money but to send a message.
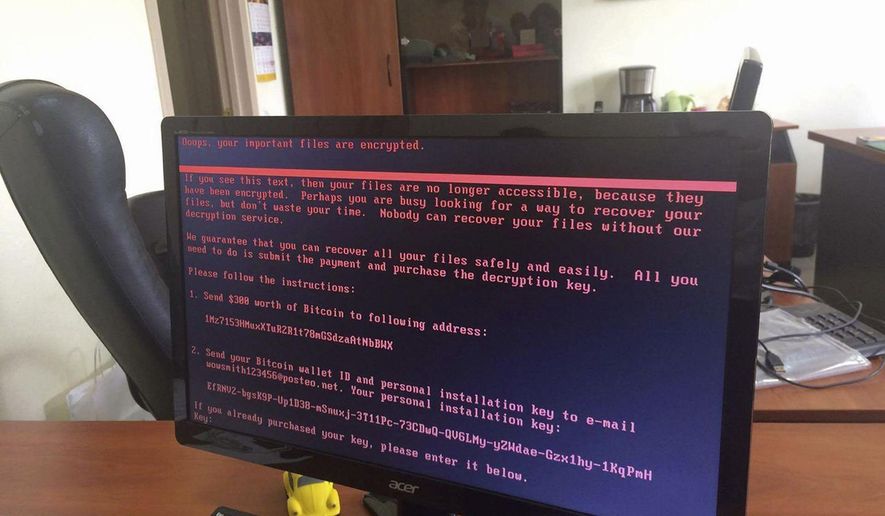
Ransomware, which has been powered by the growth of digital currencies such as Bitcoin, is a fast-growing and lucrative market for cybercriminals. It works by scrambling computers’ data, only unscrambling it in return for money.
But Matthieu Suiche, founder of Dubai-based Comae Technologies, said in a blog post that the engineering of the bug suggested that those behind it had no intention of ever retrieving the data, even if they were paid. In other words, he said in a telephone interview, the ransom demand was “a mega-diversion.”
___
6:45 p.m.
Russian President Putin says foreign intelligence agencies are conducting cyberattacks against Russia.
Speaking at the headquarters of the Russian foreign intelligence agency SVR, Putin said in comments carried by Russian news agencies on Wednesday that Russia is “witnessing a hike in activities by foreign intelligence agencies aimed against Russia and its allies.” He singled out cyberattacks as one of the ways other countries try to gain sensitive information about Russia.
Ukraine and Russia appeared hardest hit in a new strain of malicious software that froze computers around the globe on Tuesday and Wednesday. Russia’s biggest oil company, Rosneft, said Wednesday it has faced some problems but added that it was too early to assess the damage from the malicious software.
___
1:50 p.m.
The day after a particularly virulent strain of ransomware burst across the globe, the mysterious Shadow Brokers group has re-emerged to taunt the U.S. National Security Agency.
It’s a possible hint at the shadowy spy games being played behind the scenes of the cybersecurity crisis.
The Shadow Brokers, who have spent nearly a year publishing some of the American intelligence community’s most closely guarded secrets, posted a new message to the user-driven news service Steemit on Wednesday carrying new threats, a new money-making scheme and nudge-nudge references to the ransomware explosion that continues to cause disruption from Pennsylvania to Tasmania.
“Another global cyber attack is fitting end for first month of theshadowbrokers dump service,” the group said, referring to a subscription service which purportedly offers hackers early access to some of the digital NSA’s break-in tools. “There is much theshadowbrokers can be saying about this but what is point and having not already being said?”
___
1:40 p.m.
Kaspersky Lab says a massive cyberattack that has locked computers across the world involved a new malware.
The company said Wednesday that its preliminary findings suggest that it is not a variant of Petya ransomware, as some reports indicated, but a new ransomware that has not been seen before.
It named it ExPetr, noting that “while it has several strings similar to Petya, it possesses entirely different functionality.”
The company said its telemetry data indicates around 2,000 attacked users so far. It added that organizations in Russia and Ukraine were the most affected, and hits were also registered in Poland, Italy, the U.K., Germany, France, the U.S. and several other countries.
It added that the cyberattack involved modified EternalBlue and EternalRomance exploits.
___
1:35 p.m.
The Ukrainian Cabinet says an outburst of malicious software has been contained.
The ransomware that paralyzed computers across the world hit Ukraine hardest Tuesday, with victims including top-level government offices, energy companies, banks, cash machines, gas stations, and supermarkets.
The Cabinet said in Wednesday’s statement that the cyber-assault has been stopped and the situation now is under “full control.”
It added that “all strategic assets, including those involved in protecting state security, are working normally.”
Ukrainian railways said in a separate statement that the cyberattack has caused some disruptions with money transactions, but its operations haven’t been affected.
___
1:20 p.m.
Russia’s Rosneft oil company says some of its gas stations have been affected by the outbreak of malicious software, but production operations haven’t been hurt.
The company said Wednesday it’s too early to assess the damage from malicious software that has crippled computers across the world.
It acknowledged that it has faced some problems, which are being dealt with quickly. Rosneft said cash registers at some of its gas stations have been affected, but didn’t offer further details.
Rosneft emphasized that its production cycle hasn’t been affected by ransomware.
___
1:10 p.m.
The Kremlin says that a ransomware attack that has affected computers across the world highlights the need for close international cooperation in fighting cybercrime.
Russian President Vladimir Putin’s spokesman Dmitry Peskov said the attack “again proves the Russian thesis that such a threat requires cooperation on the global level.”
Ukraine and Russia appeared hardest hit by Tuesday’s violent outbreak of data-scrambling software that locks up computer files with all-but-unbreakable encryption and then demands a ransom for its release. In the United States, the malware affected companies such as the drugmaker Merck and Mondelez International, the owner of food brands such as Oreo and Nabisco.
Peskov said Wednesday that “no country can efficiently tackle cyber threats alone.” He added that the attack hasn’t caused any serious disruptions in Russia.
___
1:05 p.m.
Operations at a terminal at India’s busiest container port have been stalled by the malicious software that suddenly burst across the world’s computer screens Tuesday, another example of the disruption that continues to be felt globally.
M.K. Sirkar, a manager at the Jawaharlal Nehru Port Trust in Mumbai, said Wednesday the problem involved a terminal operated by A.P. Moller-Maersk. Sirkar said that no containers could be loaded or unloaded at the terminal.
In a statement, the Denmark-based group acknowledged that its APM Terminals had been “impacted in a number of ports” and that an undisclosed number of systems were shut down “to contain the issue.”
The malware has been blamed for disruption from Ukraine to Tasmania, where an Australian official said the Cadbury chocolate factory had stopped production.
___
1:00 p.m.
Experts say this week’s cyberattack had a far smaller impact on China than a similar virus in May, which caused widespread disruption.
By midday Wednesday, the Petya virus was detected in the Chinese capital, Beijing; the southern province of Guangdong near Hong Kong and in Jiangsu province, adjacent to Shanghai, said Kingsoft Corp. in a statement. The company is one of China’s biggest software suppliers.
The virus infected only one-tenth as many computers as May’s WannyCry, according to Kingsoft, a supplier of security software. It gave no other details.
The May attack disabled computers in schools, hospitals and companies in China, where widespread use of unlicensed software left systems vulnerable.
The Chinese internet regulator and police ministry did not respond to questions about how many computers were affected or how authorities were responding.
___
10:10 a.m.
Danish shipping giant A.P. Moller-Maersk, which was hit by malicious software that is crippling computers globally, says it has “contained the issue.”
The Copenhagen-based group says its APM Terminals have been “impacted in a number of ports,” adding vessels with Maersk Line were “maneuverable, able to communicate and crews are safe.”
In a statement, Maersk said Wednesday they “have shut down a number of systems to help contain the issue,” while several entities including its oil, tankers and drilling activities “are not operationally affected.”
The group said it is working on a technical recovery plan with key IT partners and global cybersecurity agencies, and is continuing to assess and manage the situation “to minimize the impact on our operations, customers and partners from the current situation.”
___
10 a.m.
An official says operations at a terminal at India’s busiest container port have been stalled by the malicious software that has crippled computers globally.
M.K. Sirkar, a manager at the Jawaharlal Nehru Port Trust in Mumbai, said the problem involved a terminal operated by A.P. Moller-Maersk. Sirkar said that no containers could be loaded or unloaded at the terminal Wednesday.
He said that an emergency response team at the port was in touch with Microsoft to fix the problem as soon as possible. He said that officials were also trying to figure out a manual workaround at the affected terminal.
He added that any response would take time to implement given the large volume of traffic handled by the port.
___
7:30 a.m.
Australia’s government says two Australian companies have been struck by a ransomware attack that is likely the same virus affecting computers across the world.
Australia’s Cyber Security Minister, Dan Tehan, told reporters on Wednesday that officials have yet to confirm that the Australian companies were hit by the same strain of ransomware that has struck hospitals, government offices and corporations across the world. But Tehan said “all indications would point to” it being the same virus.
Tehan did not name the companies affected. But earlier Wednesday, the Australian Manufacturing Workers’ Union’s Tasmania secretary John Short said the Cadbury chocolate factory in Tasmania had stopped production after computers there crashed.
___
7 a.m.
A highly virulent strain of malicious software that is crippling computers globally appears to have been sown in Ukraine, where it badly hobbled much of the government and private sector on the eve of a holiday celebrating a post-Soviet constitution.
Hospitals, government offices and major multinationals were among the casualties of the ransomware payload, which locks up computer files with all-but-unbreakable encryption and then demands a ransom for its release.
In the United States, it affected companies such as the drugmaker Merck and food conglomerate Mondelez International. The virus’ pace appeared to slow by Wednesday, in part because the malware appeared to require contact between computer networks.



Please read our comment policy before commenting.